In 2017, the number of command and control (C&C) servers used for managing IoT botnets has more than doubled, going from 393 in 2016 to 943 in 2017.
The number is based on statistics provided by Spamhaus, an organization that aggregates data on abusive web hosts as part of several blacklists.
Botnets IP total grew by 32%
In a summary report for the past year, Spamhaus says it indexed over 9,500 new botnet C&C servers in 2017, a 32% increase from the previous year.
This number includes the IP addresses of C&C servers for botnets made up from many types of devices, not just IoT devices.
The 9,500+ figure also includes detections of C&C servers for all sorts of cybercrime activity, such as C&C servers used to control DD0S botnets, spam networks, banking trojans, or servers where crooks send data collected from phishing kits and infostealer malware.
Crooks preferred buying servers instead of hacking them
Of the 9,500 new botnet C&C servers that popped up in 2017, Spamhaus says that the vast majority —6,588 IP addresses, or 68% of the total— were IP addresses that linked back to individual servers that have been purchased from web hosting companies for the sole purpose of hosting malware operations.
The rest of the 9,500+ IPs Spamhaus indexed represent botnet C&C servers hosted on hacked servers. The proportion between bought and hacked servers used in malware and cybercrime operations remained the same as in 2016, according to the report.
Pony reigned supreme
The most common type of C&C server Spamhaus indexed was for a malware named Pony, an information-stealing trojan that can collect passwords from infected devices, and optionally drop other malware.
Because IoT malware usually evolves from one another and malware families are so intertwined with one another, detections for different IoT botnets were all mashed together. When aggregated, IoT botnets ranked second behind Pony as the most common C&C servers found in 2017.
Below is a chart of the Top 20 most common botnet C&C servers indexed by Spamhaus, along with other stats published in the Spamhaus report.
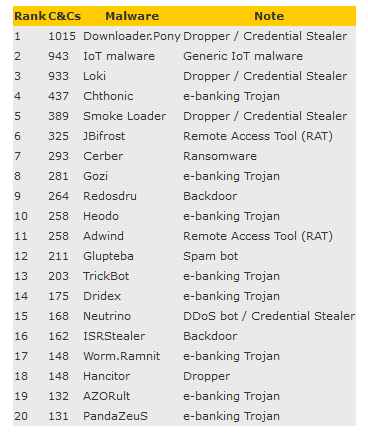
⁘ C&C servers for ransomware operations changed from 2016. Locky and TorrentLocker fell out of the Top 20, while Cerber landed on #7.
⁘ Java-based RATs like JBifrost (#6) and Adwind (#11) entered the top 20 after Java-based malware was very popular all last year.
⁘ On average, Spamhaus added between 600 to 700 new IP addresses to its blacklist of C&C servers hosted on legitimate hosting provider infrastructure (BCL - Botnet Controller List — a "drop all traffic" blacklist).
⁘ OVH and Amazon hosted the most BCL entries.
Namecheap to blame for 25% of all C&C server domains
But besides IP addresses, Spamhaus also kept track and created a blacklist for domain names —the Spamhaus DBL— in case crooks decided to hide C&C servers behind generic domains instead of IP addresses.
Spamhaus says that crooks usually prefer using domain names and rented VPS systems instead of IP addresses and hacked servers. The organizations' experts explain below:
This penchant for using domain names for the C&C server instead of IP addresses is easy to see in year-end statistics. According to Spamhaus, the organization's DBL recorded over 50,000 new domain names used for botnet C&C servers in 2017.
Based on Spamhaus data, crooks usually employed .com and .pw domains, and registered more than a quarter of all C&C botnet servers through Namecheap, a US-based domain registrar.
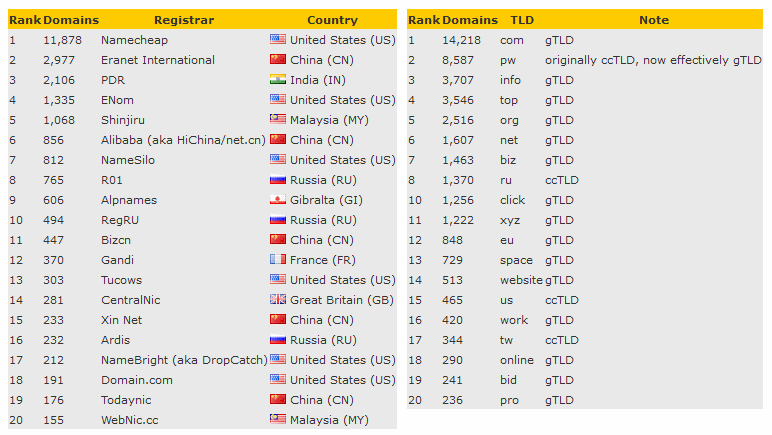
Image credits: Spamhaus


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now